Why you need to setup secure software development lifecycle (SSDLC)
Rising trend of hacker attacks on the business and government
organizations brings us to the necessity to do extra actions to
mitigate this risks.
Top 3 vectors of hacker attacks:
1. Exploiting vulnerability in the system
2. Social engineering over employees of the organization
3. Misconfiguration of a system within organization
All this three directions requires our attention right now which
means extra expenditures. How much would it cost?
Public reports shown business lost from 500k to 3.8 millions USD
in average per attack. Of course, it doesn't cover incidents
which doesn't have prices, e.g. hacking attack on nuclear plant
with worldwide disaster. Nevertheless this numbers gives us some
upper bound on how much business find reasonable to spend on
their information security.
Reports also shown current business expenditures on information
security are ~375k USD per year for large enterprises and ~38k
USD per year for small and medium businesses. Data doesn't give
us details, but likely the budget goes to buy and maintain
specialized InfoSec software, staff training and penetration
testing of the organization. It should cover point 2 and 3 from
the top list above (*), but what should be done to cover the top most
popular vector of attacks?
Professional community insists on extending software development
lifecycle (SDLC) by *secure* software development lifecycle (SSDLC).
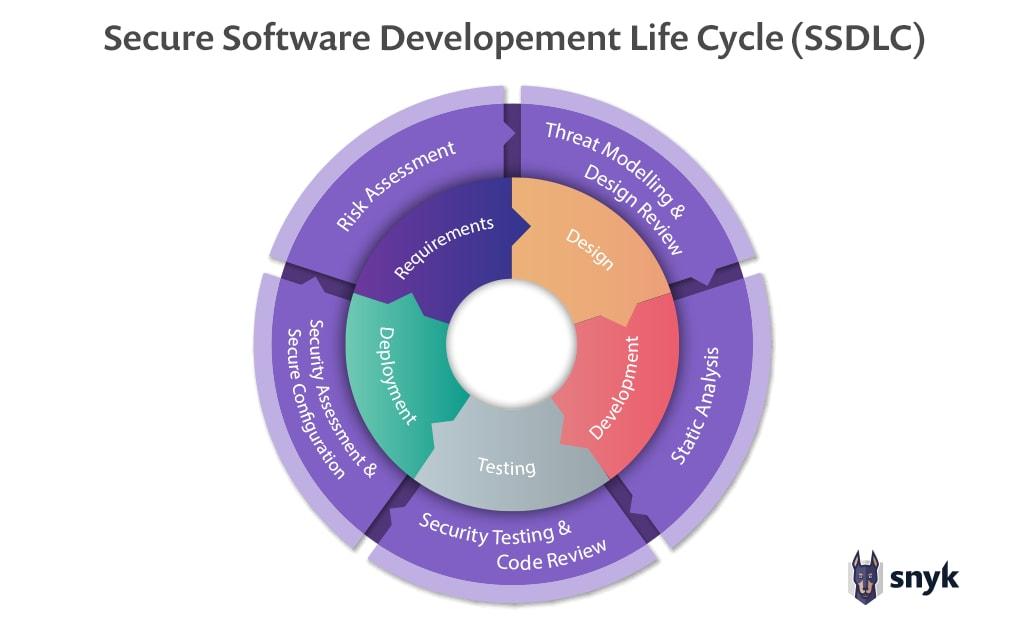
Generally speaking it means applying several practices of information security expert to each stage of software development:
Threat modelling at the design stage ->
static analyzers and security scanners at the development stage ->
penetration testing before the UAT stage.
By my ballpark estimates it will increase costs of software development by extra 25% by growing rates of SDE professionals and total amount of hours spent on the project. Of course, customers might continue develop their projects as is, but it would mean continue ignoring the top №1 cause of losses due hacker attacks.
Just sharing.
(*) organization's investments into specialized information security solutions will also in some extent mitigate part of attacks by exploiting vulnerability in the software; in which extent - is a topic of another research
Case study: establish an information security of a government organization